You must be concerned about your system security, if you are running ADF runtime based on ADF 11.1.2.1.0 - 11.1.2.4.0 versions. These versions are using JSF 2.0, with known security vulnerability - Two Path Traversal Defects in Oracle's JSF2 Implementation. This vulnerability allows to download full content of WEB-INF through any browser URL. There is a fix, but this fix is not applied by JDeveloper IDE automatically, when creating new ADF application. To prevent WEB-INF content download, you must set javax.faces.RESOURCE_EXCLUDES parameter in web.xml - make sure to provide all file extensions, you want to prevent to be accessible through URL.
By default, when vulnerability fix is not applied, we can access WEB-INF content using similar path: http://host:port/appname/faces/javax.faces.resource.../WEB-INF/web.xml. Unless you want to allow your users to download the source code, make sure to apply the fix in web.xml manually:
My test case - VulnerabilityTestCase.zip (this sample comes with vulnerability fix disabled - default version) is implemented with JDeveloper 11.1.2.4.0, I will demonstrate how to reproduce JSF 2.0 vulnerability with this version:
Test case consists of two basic applications, one of them is packaged as ADF library:
ADF library is imported into main sample application:
Two reproduce vulnerability is pretty easy - run main sample application, login with redsam/welcome1 user:
Default URL is generated in the browser and first page is rendered - all good so far:
1. web.xml vulnerability
Remove main page name and after faces/ type javax.faces.resource.../WEB-INF/web.xml, you will access web.xml content:
2. weblogic.xml vulnerability
Access content with javax.faces.resource.../WEB-INF/weblogic.xml:
3. Local ADF Task Flows vulnerability
Access in WEB-INF, using Task Flow path and name:
4. ADF Library JAR vulnerability
All ADF Library JAR's by default are packaged into WEB-INF folder, this means we could download these JARs and get entire code. You only need to type JAR file name. It is possible to get JAR file names from ADF BC configuration file, for such JAR's imported into ADF Model:
5. adfm.xml configuration file vulnerability
Here we can get a list of DataBinding files:
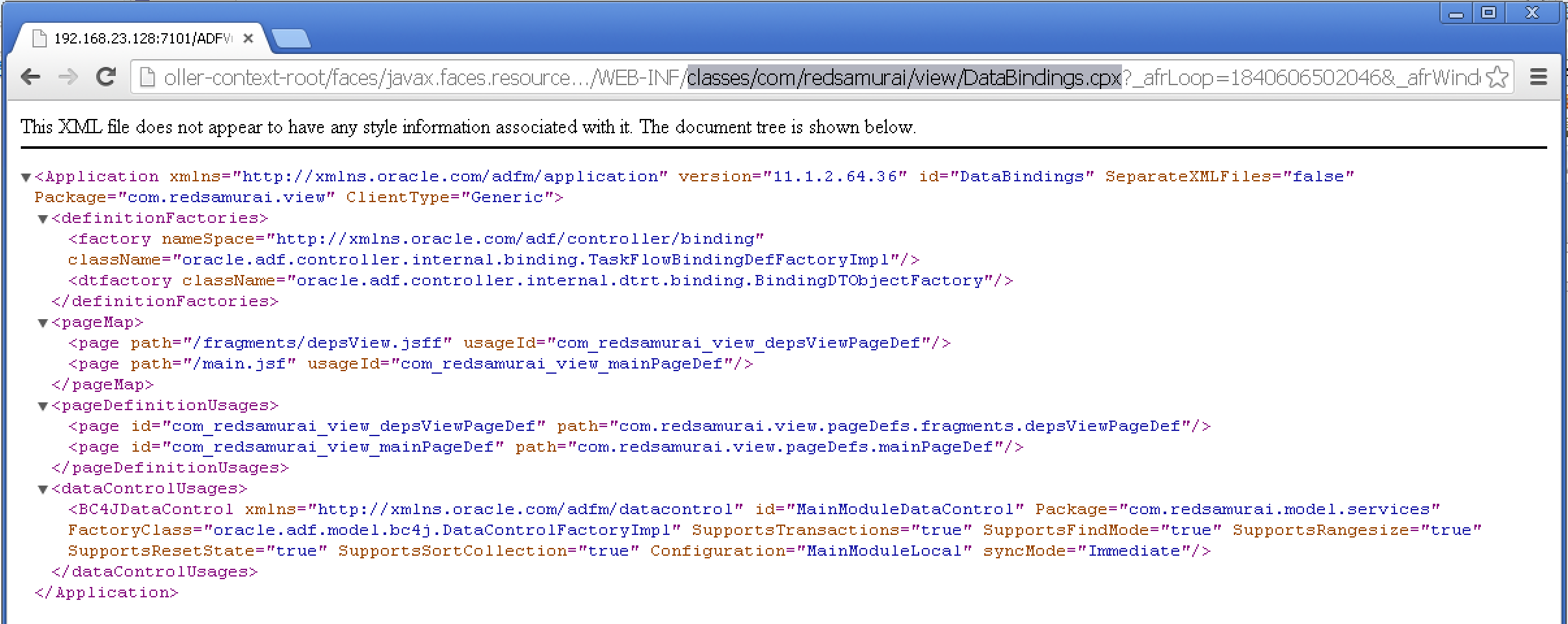
6. DataBindings.cpx file vulnerability
We have a list of DataBindings files from previous step. No we could open each DataBindings file and get a list of pages/fragments together with Page Definition mappings. We can read path information for ADF BC:
7. ADF BC vulnerability
Based in ADF BC path information from previous step, we could access Model.jpx file and read information about ADF BC packages:
8. ADF BC configuration vulnerability
We could go down and download every ADF BC component - EO/VO/AM. From bc4j.xcfg we can read info about each AM configuration, data source name, etc.:
By default, when vulnerability fix is not applied, we can access WEB-INF content using similar path: http://host:port/appname/faces/javax.faces.resource.../WEB-INF/web.xml. Unless you want to allow your users to download the source code, make sure to apply the fix in web.xml manually:
My test case - VulnerabilityTestCase.zip (this sample comes with vulnerability fix disabled - default version) is implemented with JDeveloper 11.1.2.4.0, I will demonstrate how to reproduce JSF 2.0 vulnerability with this version:
Test case consists of two basic applications, one of them is packaged as ADF library:
ADF library is imported into main sample application:
Two reproduce vulnerability is pretty easy - run main sample application, login with redsam/welcome1 user:
Default URL is generated in the browser and first page is rendered - all good so far:
1. web.xml vulnerability
Remove main page name and after faces/ type javax.faces.resource.../WEB-INF/web.xml, you will access web.xml content:
2. weblogic.xml vulnerability
Access content with javax.faces.resource.../WEB-INF/weblogic.xml:
3. Local ADF Task Flows vulnerability
Access in WEB-INF, using Task Flow path and name:
4. ADF Library JAR vulnerability
All ADF Library JAR's by default are packaged into WEB-INF folder, this means we could download these JARs and get entire code. You only need to type JAR file name. It is possible to get JAR file names from ADF BC configuration file, for such JAR's imported into ADF Model:
5. adfm.xml configuration file vulnerability
Here we can get a list of DataBinding files:
6. DataBindings.cpx file vulnerability
We have a list of DataBindings files from previous step. No we could open each DataBindings file and get a list of pages/fragments together with Page Definition mappings. We can read path information for ADF BC:
7. ADF BC vulnerability
Based in ADF BC path information from previous step, we could access Model.jpx file and read information about ADF BC packages:
8. ADF BC configuration vulnerability
We could go down and download every ADF BC component - EO/VO/AM. From bc4j.xcfg we can read info about each AM configuration, data source name, etc.:













8 comments:
Hi Andrejus
Thanks for sharing ! I'm not sure, but I think this issue is known by Oracle as CVE-2013-3827 and a fix is included in CPU (critical patch update) of October 2013. Please check with Oracle to confirm this.
Luc
Goal of this post is to inform ADF users about the issue - as it is reproduced in JDEV 11g R2 releases downloaded from OTN. I prefer to inform community. If Oracle could confirm patch number, follow up on this post is welcome.
In the next post - I will describe another security issue, reproduced in 12c and 11g R2, related to Facelets.
Andrejus
Luc is correct this was addressed back in October's CPU
This is good.
Andrejus
Hi,
I installed the SU Patch FCX7 to upgrade my WLS to 10.3.6.0.7 but unfortunately this doesn't solve the security issue. I still need the web.xml context parameters. So it seems the issue is not fixed in the latest SU Patch.
Steven?-.
Hi Steven,
May be you need to apply a patch from October 2013 also, as latest patch may not include all the fixes from previous patches.
Regards,
Andrejus
Hi Andrejus,
After re-reading the documentation of the Critcial Patch Update (Doc ID 1571391.1), I noticed that I only applied the Oracle WLS Patch and not the Oracle JDeveloper patch.
For ADF 11.1.2.4.0 you have to install patch #17308379. Once this path is applied the content of the WEB-INF folder is no longer displayed. Their is no need to set the web.xml context parameter javax.faces.RESOURCE_EXCLUDES.
Regards,
Steven.
Perfect. Thanks for sharing. All other users will be informed.
Regards,
Andrejus
Post a Comment